-
06.05.2010 01:41:27
Blocking w00tw00t.at.ISC.SANS.DFind:) with iptables
How i got rid of the w00tw00t entries in my server logs
from: cpom | Comments: 0 -
The first encounter with w00tw00t.at.ISC.SANS.DFind:) was for me around January 2010. I saw it in one of my server logs and didnt think about this very much. Later, around the mid of February, the frequency began to grow and in march 2010 this wootwoot vulnerabilty scanner thing hit up to 20 times a day on my site.
And not enough: a minute or two later after each wootwoot hit, between 100 -1000 requests hit in, searching for vulnerable joomla, phpMyAdmin, oscommerce or other PHP based software installations. I do not run any PHP software (PHP isnt even installed) and I didnt need to worry, it made me very angry.
I was told from a lot of people to ignore it, but let me ask a question: Would you ignore people, who throw small stones at your door twenty times a day, only to see if the door is vulnerable?
Searching for a Solution
I have been searching for a long time to find an acceptable solution. I tried to setup rewrite rules within Apaches config files. No success. I tried blocking this requests via some regex settings within my proxy server. No success. And I tried catching and redirect it within my web applications. And again: No success.
On the other hand: It helped me a lot to harden my server configurations and to close the small holes that exist in every setup. And I have learned: every web server responds different to w00tw00t.
As I understand the HTTP Specification, a GET /w00tw00t.at.ISC.SANS.DFind:) should result in a HTTP 400: Bad Request response from your web server. This is the case if you use one or another ASP.Net-Server. The in one or another way preconfigured Apache servers from mass hosters return a HTTP 404 : Not found. And last but not least: Some application servers respond with a HTTP 500: Internal server error, which is very bad if you are caching content in a reverse proxy because the proxy server delivers this error site to the next 20 - 30 requesting clients.
Finally I found a solution
I thought, I will never get rid of this %&?§* message and the spam kids will always throw stones at my door. Then I read about iptables and its ability to filter strings. That was enlightening. It took me 5 minutes to search the net and find a solution here. A simple:
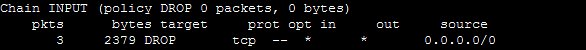
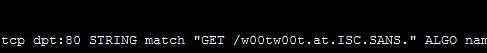
/sbin/iptables -I INPUT -d MY.IP.ADR.HRE -p tcp --dport 80 -m string --to 70 \ --algo bm --string 'GET /w00tw00t.' -j DROP
on my linux box made me sleep much better. It is not a very sophisticated solution, one might say: brutal because it filters all incoming packages, but it works.
Because I do not have a high traffic web site, this setting does not cause any trouble to me. If you are interested in a much smarter solution and a detailed explanation of w00tw00t have a look at spamcleaner.org, the site where I found my solution. Good Luck !
Update [07/05/2010]
I posted this blog entry on reddit.com and a lot of people responded. Many agreed with me, but a lot of people strongly disagreed. Here are the essence:
- If you are realy sure there is an automtic scanner behind this w00w00t messages, ignoring the log entries could be an option
- Deeper inspection of all incoming packets (seraching for matching strings) on port 80 is a complete overkill, using this on a daily basis is not reccomended
- "This solution is like hitting a fly with a sledgehammer ...", also auf gut deutsch: "Holzhammer-Methode !"
- If you are not sure these messages are send automaticly, use an intrusion detection system like snort
- A funny guy send a request to this server with "/w00tw00t.hi.claudius" (Claudius, thats -> me). Hello stranger ! I adapted my iptables rule
- The last 24 hours this server was hit by around 300 w00tw00t packages. In hight times (before filtering it out) this number was between 3500 - 4000
I would like to thank all people who read this entry and especially those who responded on reddit.
Kommentar hinzufügen | nach oben
- If you are realy sure there is an automtic scanner behind this w00w00t messages, ignoring the log entries could be an option
- Comments are disabled
Neueste Artikel:
- Team Foundation Service Preview TFS in the Cloud von: cpom
- Ein erster Eindruck von Visual Studio 11 Express von: cpom
- Ein erster Eindruck von TFS 11 Express von: cpom
- Disabling IPv6 in Windows 7 or Vista von: cpom
- Die Wiederbelebung von: cpom
Kommentare augeschaltet